My Blogs
Sample integration iDempiere with Blockchain Hyperledger Fabric
In this is blog I want to describe as we can use the integration iDempiere ERP Business Suite with Demo Tuna Network which tracks a tuna’s story from its capture till a chef cooks it.
The iDempiere as a client application will be used to send transactions to the blockchain and Hyperledger Fabric’s framework to keep track of each part of this process. As ideal we can use one instance of iDempiere on the Cloud and create new clients for each members ot this business process. But other members can use different Desktop/Mobile applications wich have integrate to the Blockchain.
I used information from this course and changed Javascript Application to iDempiere for more understunding of integration.
Lets go ...
Problem Context:
With the Tuna 2020 Traceability Declaration (real document) in mind, our goal is to eliminate illegal, unreported, and unregulated fishing. We will use Hyperledger Fabric to bring transparency and clarity to a real-world example: the supply chain of tuna fishing.
We will be describing how tuna fishing can be improved, starting from the source, fisherman Sarah, and the process by which her tuna ends up at Miriam’s restaurant. In between, we’ll have other parties involved, such as the regulator who verify the validity of the data and the sustainability of the tuna catches.
P.S. There are a lot of legal problems in many industries as Finance (money laundering), Insurance(illegal insurance) , Healthcare(fraudulent medicines), Logistic(improper storage, such as storage above or below a specific temperature etc), Manufacturing (fraudulent materials, parts etc.), etc which we can solve with Business Blockchain.
We will be using Hyperledger Fabric’s framework to keep track of each part of this process and you can see transaction flow below and read descriptions as it work.
Stakeholders:
1) Sarah is the fisherman who sustainably and legally catches tuna.
After each catch, Sarah records information about each individual tuna, including: a unique ID number, the location and time of the catch, its weight, the vessel type, and who caught the fish. For the sake of simplicity, we will stick with these six data attributes. However, in an actual application, many more details would be recorded, from toxicology, to other physical characteristics.
These details are saved in the world state as a key/value pair based on the specifications of a chaincode contract, allowing Sarah’s application to effectively create a transaction on the ledger.
2) Miriam | Restaurant Owner | Buyer who will serve as the end user, in this situation.
Miriam is a restaurant owner looking to source low cost, yet high quality tuna that have been responsibly caught. Whenever Miriam buys tuna, she is always uncertain whether she can trust that the tuna she is purchasing is legally and sustainably caught, given the prominence of illegal and unreported tuna fishing.
At the same time, as a legitimate and experienced fisherman, Sarah strives to make a living selling her tuna at a reasonable price. She would also like autonomy over who she sells to and at what price.
3) Carl is another restaurant owner fisherman Sarah can sell tuna to.
Normally, Sarah sells her tuna to restaurateurs, such as Carl, for $80 per pound. However, Sarah agrees to give Miriam a special price of $50 per pound of tuna, rather than her usual rate. In a traditional public blockchain, once Sarah and Miriam have completed their transaction, the entire network is able to view the details of this agreement, especially the fact that Sarah gave Miriam a special price. As you can imagine, having other restaurateurs, such as Carl, aware of this deal is not economically advantageous for Sarah.
To remedy this, Sarah wants the specifics of her deal to not be available to everyone on the network, but still have every actor in the network be able to view the details of the fish she is selling. Using Hyperledger Fabric’s feature of channels, Sarah can privately agree on the terms with Miriam, such that only the two of them can see them, without anyone else knowing the specifics.
Additionally, other fishermen, who are not part of Sarah and Miriam’s transaction, will not see this transaction on their ledger. This ensures that another fisherman cannot undercut the bid by having information about the prices that Sarah is charging different restaurateurs.
4) Regulators | Contract Enforcers verify that the tuna has been legally and sustainably caught.
Regulators will also gain entry to this Hyperledger Fabric blockchain network to confirm, verify, and view details from the ledger. Their application will allow these actors to query the ledger and see the details of each of Sarah’s catches to confirm that she is legally catching her fish.
Regulators only need to have query access, and do not need to add entries to the ledger. With that being said, they may be able to adjust who can gain entry to the network and/or be able to remove fishermen from the network, if found to be partaking in illegal activities.
Gaining Network Membership
Hyperledger Fabric is a permissioned network, meaning that only participants who have been approved can gain entry to the network. To handle network membership and identity, membership service providers (MSP) manage user IDs, and authenticate all the participants in the network.
In our scenario, the regulator, the approved fishermen, and the approved restaurateurs should be the only ones allowed to join the network.
Our scenario has two separate chaincodes, which are run on three separate channels.Chaincodes
1. One for the price agreement between the fisherman and the restaurateur
2. One for the transfer of tuna.
Channels
1. One for the price agreement between Seller (Sarah) and Buyer (Miriam)
2. One for the price agreement between Seller (Sarah) and Buyer (Carl)
3. One for the transfer of tuna.
Each member of this network knows about each other and their identity. The channels provide privacy and confidentiality of transactions.Demo Tuna Network Architecture
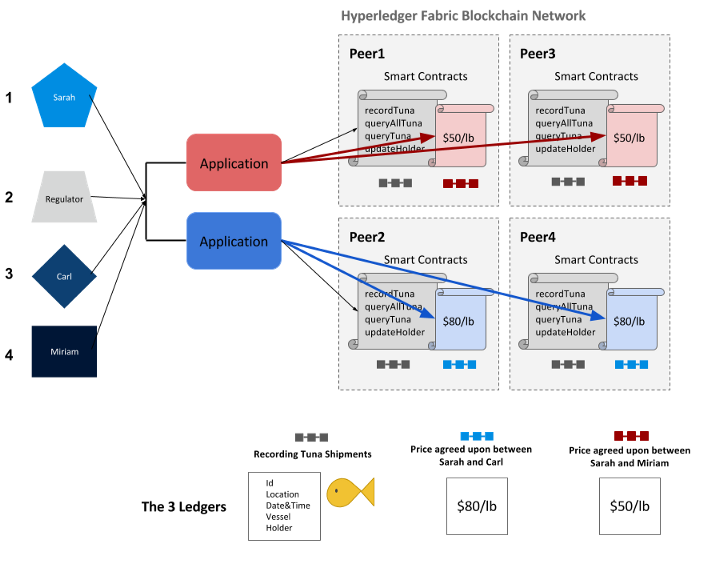
Below is a summary of the tuna catch scenario presented in this section:
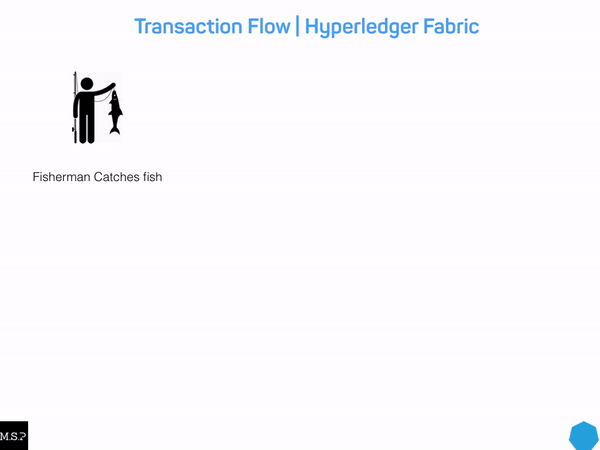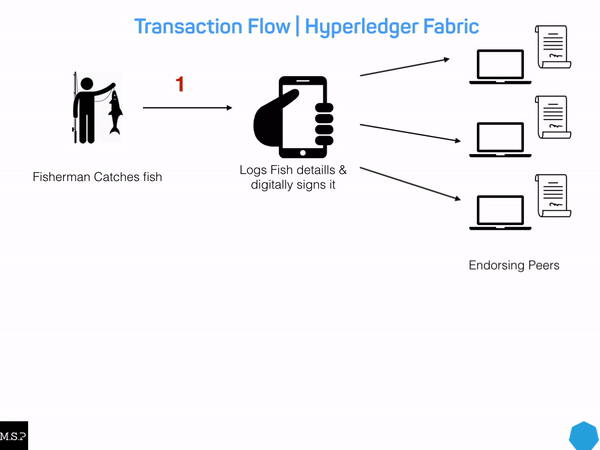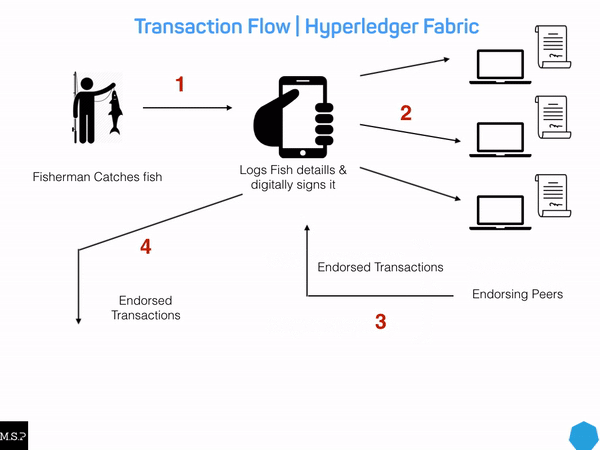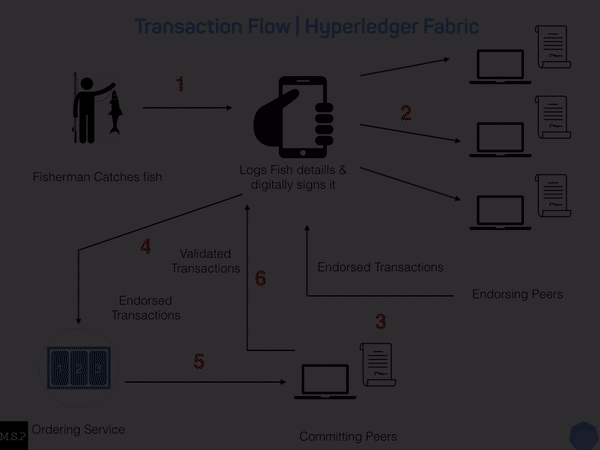
1. Sarah catches a tuna and uses the supply chain application’s user interface to record all the details about the catch to the ledger. Before it reaches the ledger, the transaction is passed to the endorsing peers on the network, where it is then endorsed. The endorsed transaction is sent to the ordering service, to be ordered into a block. This block is then sent to the committing peers in the network, where it is committed after being validated.
2. As the tuna is passed along the supply chain, regulators may use their own application to query the ledger for details about specific catches (excluding price, since they do not have access to the price-related chaincode)
3. Sarah may enter into an agreement with a restaurateur Carl, and agree on a price of $80 per pound. They use the blue channel for the chaincode contract stipulating $80/lb. The blue channel’s ledger is updated with a block containing this transaction.
4. In a separate business agreement, Sarah and Miriam agree on a special price of $50 per pound. They use the red channel’s chaincode contract stipulating $50/lb. The red channel’s ledger is updated with a block containing this transaction.
Hyperledger Fabric Elements whitch used
1. Channels are data partitioning mechanisms that allow transaction visibility for stakeholders only. Each channel is an independent chain of transaction blocks containing only transactions for that particular channel.
2. Chaincode /(Smart Contract) | It encapsulates both the asset definitions and the business logic (or transactions) for modifying those assets. Transaction invocations result in changes to the ledger.
3. Ledger contains the current world state of the network and a chain of transaction invocations. A shared, permissioned ledger is an append-only system of records and serves as a single source of truth.
4. Network is the collection of data processing peers that form a blockchain network. The network is responsible for maintaining a consistently replicated ledger.
5. Ordering Service is a collection of nodes that orders transactions into a block.
6. World State reflects the current data about all the assets in the network. This data is stored in a database for efficient access. Current supported databases are LevelDB and CouchDB.
7. Membership Service Provider (MSP) manages identity and permissioned access for clients and peers.
Thank you for your kind attention.